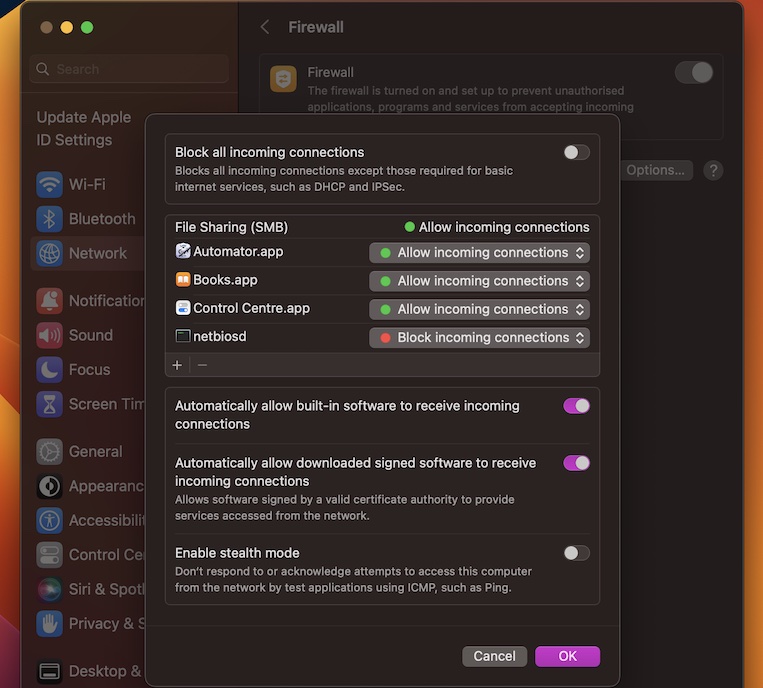
In today's interconnected world, the Internet of Things (IoT) plays a pivotal role in enhancing productivity, efficiency, and automation. However, integrating IoT devices into secure networks, such as those behind firewalls, presents challenges for organizations and individuals alike. This article delves into the process of using RemoteIoT behind firewalls with a Mac server as an example. Whether you're a tech enthusiast or an IT professional, this guide will provide you with the knowledge and tools needed to securely manage IoT devices within your network.
With the rapid advancement of technology, IoT devices are becoming increasingly common in homes and businesses. However, ensuring their seamless operation while maintaining network security is crucial. This article explores how to set up and manage RemoteIoT devices behind firewalls using a Mac server, providing practical solutions and expert advice.
By the end of this article, you'll have a comprehensive understanding of the technical aspects involved in setting up RemoteIoT, configuring firewalls, and utilizing a Mac server to ensure secure communication. Let's dive in and explore this exciting topic!
Read also:Big Booty Bailey Video
Table of Contents
- Introduction to RemoteIoT
- Understanding Firewalls
- Mac Server Basics
- Setting Up RemoteIoT
- Configuring Firewall
- Using Mac Server
- Security Best Practices
- Troubleshooting Common Issues
- Real-World Examples
- Conclusion
Introduction to RemoteIoT
RemoteIoT refers to the ability to manage and control IoT devices remotely, even when they are located behind firewalls or in secure networks. This technology enables users to interact with IoT devices from anywhere in the world, provided they have internet access.
Key benefits of using RemoteIoT include:
- Enhanced flexibility in device management
- Improved security through controlled access
- Cost savings by reducing the need for physical presence
Understanding RemoteIoT is essential for anyone looking to integrate IoT devices into their network infrastructure. It combines hardware, software, and network configurations to create a secure and efficient system.
Applications of RemoteIoT
RemoteIoT finds applications in various industries, including:
- Smart homes
- Industrial automation
- Healthcare monitoring
- Environmental control systems
Each of these applications requires a tailored approach to ensure optimal performance and security.
Understanding Firewalls
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between trusted internal networks and untrusted external networks, such as the internet.
Read also:Po Box 14371 Lexington Ky Ebt
Firewalls play a critical role in securing IoT devices, as they help prevent unauthorized access and potential cyberattacks. When setting up RemoteIoT behind a firewall, it's essential to configure the firewall correctly to allow necessary traffic while blocking malicious attempts.
Types of Firewalls
There are several types of firewalls, including:
- Packet-filtering firewalls
- Stateful inspection firewalls
- Application-level gateways
- Next-generation firewalls
Each type offers unique features and capabilities, making it important to choose the right firewall for your specific needs.
Mac Server Basics
A Mac server is a powerful tool for managing networks, hosting services, and running applications. It provides a robust platform for integrating IoT devices and ensuring secure communication behind firewalls.
Key features of a Mac server include:
- High-performance hardware
- Reliable macOS operating system
- Advanced security protocols
Using a Mac server for RemoteIoT setups ensures stability, scalability, and ease of management.
Setting Up a Mac Server
To set up a Mac server, follow these steps:
- Install macOS Server on your Mac
- Configure network settings
- Set up user accounts and permissions
- Install necessary software and services
Proper configuration is crucial for optimal performance and security.
Setting Up RemoteIoT
Setting up RemoteIoT involves several steps, including configuring devices, setting up the server, and ensuring secure communication. Below is a detailed guide to help you through the process.
Step 1: Identify the IoT devices you want to manage remotely.
Step 2: Install the necessary software on your Mac server to support RemoteIoT functionality.
Step 3: Configure network settings to allow communication between the server and IoT devices.
Configuring IoT Devices
When configuring IoT devices, consider the following:
- Ensure devices are compatible with your network
- Set up secure authentication methods
- Update firmware regularly to address security vulnerabilities
By following these steps, you can ensure seamless integration of IoT devices into your network.
Configuring Firewall
Configuring a firewall for RemoteIoT involves setting up rules to allow necessary traffic while blocking unauthorized access. Below are some best practices for firewall configuration:
- Create specific rules for IoT devices
- Use port forwarding to direct traffic to the correct devices
- Implement intrusion detection and prevention systems
Proper firewall configuration is essential for maintaining network security and ensuring the smooth operation of IoT devices.
Firewall Rules for RemoteIoT
When setting up firewall rules for RemoteIoT, consider the following:
- Allow traffic on specific ports required by IoT devices
- Block all other incoming and outgoing traffic
- Regularly review and update firewall rules to address new threats
These practices help ensure a secure and efficient network environment.
Using Mac Server
Using a Mac server for RemoteIoT offers several advantages, including ease of use, reliability, and advanced security features. Below are some tips for maximizing the potential of your Mac server:
- Regularly back up server data
- Monitor server performance and resource usage
- Implement automated updates for security patches
By following these tips, you can ensure your Mac server operates at peak efficiency and provides a secure platform for managing IoT devices.
Mac Server Security Features
Mac servers come equipped with several security features, including:
- Firewall protection
- Encrypted communication protocols
- User authentication and access control
These features help safeguard your network and IoT devices from potential threats.
Security Best Practices
Ensuring the security of RemoteIoT setups requires adherence to best practices. Below are some key practices to follow:
- Use strong passwords and two-factor authentication
- Regularly update software and firmware
- Monitor network activity for suspicious behavior
By implementing these practices, you can minimize the risk of cyberattacks and protect your network and IoT devices.
Common Security Threats
Some common security threats to be aware of include:
- Malware infections
- Denial-of-service attacks
- Unauthorized access attempts
Being aware of these threats and taking proactive measures can help safeguard your network.
Troubleshooting Common Issues
When working with RemoteIoT behind firewalls, you may encounter various issues. Below are some common problems and their solutions:
- Issue: Devices unable to connect to the server
Solution: Check firewall rules and network settings - Issue: Slow communication between devices and server
Solution: Optimize server performance and network bandwidth - Issue: Security alerts triggered by legitimate traffic
Solution: Review and adjust firewall rules
Addressing these issues promptly can help maintain the efficiency and security of your RemoteIoT setup.
Diagnostic Tools
Several diagnostic tools can assist in troubleshooting RemoteIoT issues, including:
- Network analyzers
- Log monitoring software
- Performance testing tools
Using these tools effectively can help identify and resolve issues quickly.
Real-World Examples
Real-world examples of RemoteIoT setups can provide valuable insights into practical applications. Below are some examples:
Example 1: A smart home system using RemoteIoT to control lighting, temperature, and security cameras from anywhere in the world.
Example 2: An industrial automation setup where RemoteIoT is used to monitor and control machinery in real-time.
Example 3: A healthcare facility utilizing RemoteIoT for patient monitoring and equipment management.
These examples demonstrate the versatility and potential of RemoteIoT technology.
Lessons Learned
From these examples, we can learn the importance of:
- Tailoring solutions to specific needs
- Ensuring robust security measures
- Regularly updating and maintaining systems
Applying these lessons can help ensure successful RemoteIoT implementations.
Conclusion
In conclusion, using RemoteIoT behind firewalls with a Mac server as an example offers numerous benefits, including enhanced security, flexibility, and efficiency. By following the steps and best practices outlined in this article, you can successfully set up and manage IoT devices within your network.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into technology and networking. Together, let's build a safer and more connected world!