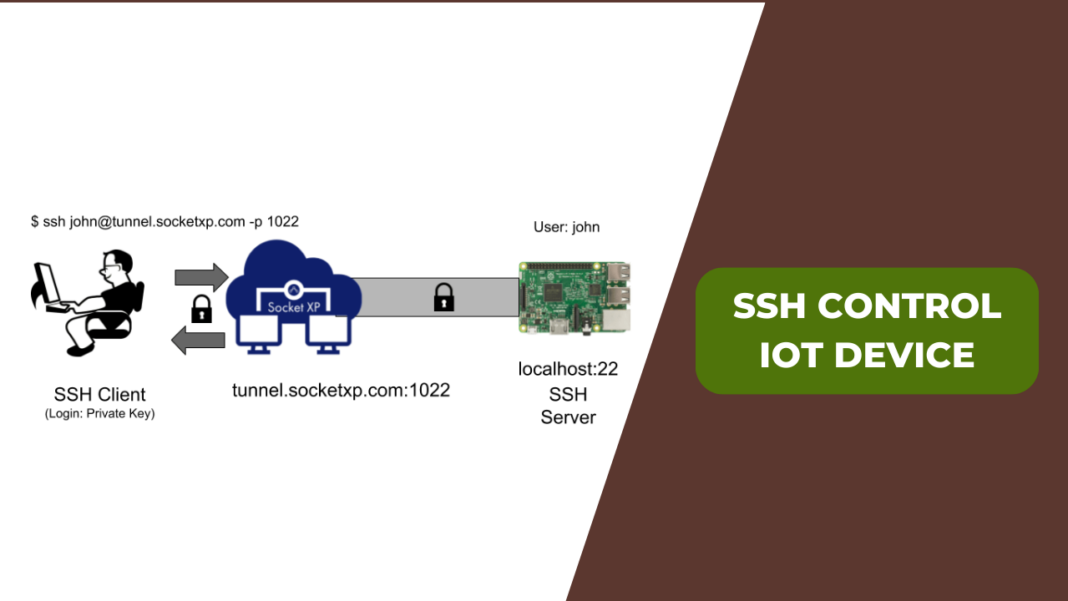
RemoteIoT devices have revolutionized the way we interact with technology, offering unparalleled flexibility and convenience. Whether you're managing industrial equipment, monitoring environmental conditions, or automating home systems, RemoteIoT devices play a critical role. To ensure secure and efficient management of these devices, understanding SSH (Secure Shell) is essential. This tutorial will guide you step-by-step through the process of configuring and managing RemoteIoT devices using SSH.
As the world becomes increasingly interconnected, the demand for secure remote access to IoT devices grows exponentially. SSH provides a secure communication channel, encrypting data and protecting sensitive information from unauthorized access. By mastering SSH, you can enhance the security of your RemoteIoT devices while maintaining ease of access and control.
This article is designed to cater to both beginners and intermediate users who want to explore the capabilities of SSH in managing RemoteIoT devices. We'll cover everything from basic concepts to advanced configurations, ensuring you have a solid foundation to build upon. Let's dive in!
Read also:Marleny Santana Erome
Table of Contents
- Introduction to RemoteIoT Devices
- What is SSH?
- Benefits of Using SSH for RemoteIoT Devices
- Setting Up SSH on RemoteIoT Devices
- Connecting to RemoteIoT Devices via SSH
- Security Best Practices for SSH
- Troubleshooting Common SSH Issues
- Advanced SSH Configurations
- Tools and Software for SSH Management
- Conclusion and Next Steps
Introduction to RemoteIoT Devices
Understanding RemoteIoT Technology
RemoteIoT devices are part of the broader Internet of Things (IoT) ecosystem, designed to enable remote monitoring and control of various systems. These devices can range from simple sensors to complex industrial machinery, all connected via the internet. The ability to access and manage these devices remotely is critical for maintaining operational efficiency and security.
Why RemoteIoT Devices are Important
The significance of RemoteIoT devices lies in their ability to streamline processes and reduce costs. By enabling remote access, businesses can minimize the need for on-site visits, saving time and resources. Additionally, these devices provide real-time data, allowing for proactive decision-making and improved system performance.
Applications of RemoteIoT Devices
RemoteIoT devices find applications in various industries, including:
- Smart homes
- Industrial automation
- Agriculture
- Healthcare
- Transportation
Each of these sectors benefits from the flexibility and security offered by RemoteIoT devices, making them an indispensable part of modern technology.
What is SSH?
Definition and Purpose
SSH, or Secure Shell, is a cryptographic network protocol designed for secure communication over unsecured networks. It provides a secure channel for accessing and managing remote devices, ensuring that data transmitted between the client and server remains encrypted and protected from interception.
Key Features of SSH
- Encryption: Protects data during transmission
- Authentication: Ensures only authorized users can access the system
- Integrity: Verifies that data has not been tampered with during transmission
These features make SSH an ideal choice for managing RemoteIoT devices, where security and reliability are paramount.
Read also:Swirling Chocolate
Benefits of Using SSH for RemoteIoT Devices
Implementing SSH for RemoteIoT devices offers numerous advantages, including enhanced security, ease of use, and flexibility. By leveraging SSH, you can ensure that your devices remain secure while maintaining seamless remote access. Below are some key benefits:
Security Enhancements
SSH encrypts all data transmitted between the client and server, making it difficult for attackers to intercept sensitive information. Additionally, SSH supports various authentication methods, including password-based and public-key authentication, providing multiple layers of security.
Efficient Remote Management
With SSH, you can manage RemoteIoT devices from anywhere in the world, as long as you have an internet connection. This flexibility allows for quick troubleshooting and system updates, reducing downtime and improving overall efficiency.
Compatibility and Scalability
SSH is compatible with a wide range of operating systems and devices, making it a versatile solution for managing diverse RemoteIoT setups. Its scalability ensures that it can handle growing networks without compromising performance or security.
Setting Up SSH on RemoteIoT Devices
Configuring SSH on your RemoteIoT devices is a straightforward process that involves a few key steps. Follow the instructions below to ensure a secure and functional setup.
Step 1: Install SSH Server
Most RemoteIoT devices come with SSH server software pre-installed. However, if it's not already installed, you can do so by running the following command:
sudo apt-get install openssh-server
This command installs the OpenSSH server, a widely used and trusted SSH implementation.
Step 2: Enable SSH Service
Once the SSH server is installed, you need to enable the service to start automatically on boot. Use the following command:
sudo systemctl enable ssh
This ensures that the SSH service is always running, ready to accept incoming connections.
Step 3: Configure Firewall Settings
To allow SSH traffic, you need to configure your firewall settings. Use the following command to open port 22, the default SSH port:
sudo ufw allow 22
By opening this port, you enable SSH connections while maintaining security for other services.
Connecting to RemoteIoT Devices via SSH
Once SSH is set up on your RemoteIoT device, you can connect to it using a variety of methods. Below are some common approaches:
Using Terminal on Linux/Mac
To connect to your RemoteIoT device from a Linux or Mac computer, open the terminal and use the following command:
ssh username@remoteiot_device_ip
Replace username with your device's username and remoteiot_device_ip with the IP address of your RemoteIoT device.
Using PuTTY on Windows
For Windows users, PuTTY is a popular SSH client. Download and install PuTTY, then enter the IP address of your RemoteIoT device and select the SSH connection type to establish a connection.
Using SSH Keys for Authentication
Instead of using passwords, you can enhance security by using SSH keys. Generate a key pair using the following command:
ssh-keygen -t rsa
Copy the public key to your RemoteIoT device using:
ssh-copy-id username@remoteiot_device_ip
This method eliminates the need for password-based authentication, reducing the risk of brute-force attacks.
Security Best Practices for SSH
While SSH provides robust security features, it's essential to follow best practices to maximize protection. Below are some recommendations:
Change Default SSH Port
Changing the default SSH port from 22 to a non-standard port can deter automated attacks. Use the following command to modify the port in the SSH configuration file:
sudo nano /etc/ssh/sshd_config
Set the Port parameter to your desired value and restart the SSH service.
Disable Root Login
Disallowing root login reduces the risk of unauthorized access. Edit the SSH configuration file and set the PermitRootLogin parameter to no.
Use Public-Key Authentication
As mentioned earlier, using SSH keys instead of passwords enhances security. Ensure that public-key authentication is enabled in the SSH configuration file by setting the PasswordAuthentication parameter to no.
Troubleshooting Common SSH Issues
Even with proper configuration, issues can arise when using SSH. Below are some common problems and their solutions:
Connection Refused
If you receive a "Connection refused" error, ensure that the SSH service is running and that the firewall allows traffic on the specified port. Check the SSH configuration file for any misconfigurations.
Authentication Failed
Authentication failures can occur due to incorrect usernames, passwords, or SSH keys. Double-check your credentials and ensure that public-key authentication is properly set up.
Timeout Errors
Timeout errors often result from network issues or incorrect IP addresses. Verify that the IP address of your RemoteIoT device is correct and that there are no network interruptions.
Advanced SSH Configurations
For users seeking more advanced functionalities, SSH offers a range of configuration options. Below are some examples:
Setting Up SSH Tunnels
SSH tunnels allow you to securely forward traffic between systems. Use the following command to create a tunnel:
ssh -L local_port:destination_host:destination_port username@remoteiot_device_ip
This command forwards traffic from the specified local port to the destination host and port via the RemoteIoT device.
Configuring SSH Multiplexing
SSH multiplexing allows multiple sessions to share a single connection, improving performance and reducing latency. Enable multiplexing by adding the following lines to your SSH configuration file:
ControlMaster auto
ControlPath ~/.ssh/sockets/%r@%h:%p
This setup creates a control socket for each connection, enabling efficient session management.
Tools and Software for SSH Management
Several tools and software solutions can simplify SSH management for RemoteIoT devices. Below are some popular options:
SSH Clients
- Terminal (Linux/Mac)
- PuTTY (Windows)
- Bitvise SSH Client (Cross-platform)
SSH Servers
- OpenSSH Server
- Droplet (For lightweight devices)
Monitoring Tools
- SSHGuard
- Fail2Ban
These tools help monitor and protect SSH connections, providing an additional layer of security.
Conclusion and Next Steps
In this comprehensive RemoteIoT device SSH tutorial, we've covered everything from the basics of SSH to advanced configurations and security best practices. By following the steps outlined in this article, you can ensure secure and efficient management of your RemoteIoT devices.
To further enhance your knowledge, consider exploring additional topics such as SSH automation, scripting, and integration with other technologies. Additionally, always stay updated with the latest security trends and updates to maintain the highest level of protection for your devices.
Feel free to leave a comment or share this article with others who may find it useful. For more in-depth guides and tutorials, explore our other articles on our website. Happy learning!